You are looking for information, articles, knowledge about the topic nail salons open on sunday near me lord of sql injection on Google, you do not find the information you need! Here are the best content compiled and compiled by the https://chewathai27.com/to team, along with other related topics such as: lord of sql injection SQL injection cheat sheet, Lord of SQLI, SQL injection order by, SQL injection payload, SQL injection bypass filter, Lord of SQLInjection, SQL injection string, SQL injection – Filter bypass (Root me)
Table of Contents
Lord of SQLInjection
- Article author: los.rubiya.kr
- Reviews from users: 2998
Ratings
- Top rated: 4.2
- Lowest rated: 1
- Summary of article content: Articles about Lord of SQLInjection The Lord of the SQLI : The Fellowship of the SQLI, 2021 | | | | | | [enter to the dungeon] | | | | | | [RULE] | | – do not attack other database | | – do … …
- Most searched keywords: Whether you are looking for Lord of SQLInjection The Lord of the SQLI : The Fellowship of the SQLI, 2021 | | | | | | [enter to the dungeon] | | | | | | [RULE] | | – do not attack other database | | – do …
- Table of Contents:

Lord of SQLInjection
- Article author: medium.com
- Reviews from users: 20009
Ratings
- Top rated: 3.4
- Lowest rated: 1
- Summary of article content: Articles about Lord of SQLInjection Line 5 and 6 is a SQL Injection problem, so the processing to prevent the direct attack against the database is shown. Lines 5 and 6 mean no … …
- Most searched keywords: Whether you are looking for Lord of SQLInjection Line 5 and 6 is a SQL Injection problem, so the processing to prevent the direct attack against the database is shown. Lines 5 and 6 mean no …
- Table of Contents:

Lord of SQL injections – CHS
- Article author: chs211.wordpress.com
- Reviews from users: 39796
Ratings
- Top rated: 4.0
- Lowest rated: 1
- Summary of article content: Articles about Lord of SQL injections – CHS Lord of SQL injections. Wolfman challenge: As white spaces should not be used I used () for bypassing the spaces. To clear the level should be admin. …
- Most searched keywords: Whether you are looking for Lord of SQL injections – CHS Lord of SQL injections. Wolfman challenge: As white spaces should not be used I used () for bypassing the spaces. To clear the level should be admin. Wolfman challenge: As white spaces should not be used I used () for bypassing the spaces To clear the level id should be admin So injection is : ‘or(id=’admin’)or’ Results in clearing the level Coming to DARKELF The challenge is simple we should not use or (or) and so we can use || And the…
- Table of Contents:
‘Lord of SQL Injection’, a site where you can learn about SQL injection vulnerabilities while capturing dungeons – GIGAZINE
- Article author: gigazine.net
- Reviews from users: 33192
Ratings
- Top rated: 4.2
- Lowest rated: 1
- Summary of article content: Articles about ‘Lord of SQL Injection’, a site where you can learn about SQL injection vulnerabilities while capturing dungeons – GIGAZINE An attack that manipulates the database illegally by executing a character string that the application does not expect is called. …
- Most searched keywords: Whether you are looking for ‘Lord of SQL Injection’, a site where you can learn about SQL injection vulnerabilities while capturing dungeons – GIGAZINE An attack that manipulates the database illegally by executing a character string that the application does not expect is called. An attack that manipulates the database illegally by executing a character string that the application does not expect is called SQL injection, and there are cases where important personal information such as credit card information and address was leaked by the attack. ‘ Lord of SQLInjection ‘ is a website that captures dungeons by making full use of such SQL injection. Lord of SQL Injection https://los.rubiya.kr/ First, access Lord of SQL Injection and click ‘[enter to the dungeon]’. It's my first time to use Lord of SQL Injection, so click ‘Join’. Enter the ID, email address, and password used in Lord of SQL Injection and click ‘Join’. Enter the ID and password you registered earlier and click ‘Login’. The screen to select the enemy is displayed. Click on the first enemy ‘gremlin’. The SQL query executed on the website and the PHP code are displayed. While referring to the PHP code, you can defeat the enemy if you can execute invalid SQL queries. In this problem, you can execute a query that returns some value, so add ‘?id=admin&pw=' or '1' = '1’ to the URL and execute. ‘GREMLIN Clear!’ is displayed and I was able to defeat the enemy safely. If you solve the problem and defeat the enemy, you will proceed to a new enemy. The problem of ‘cobolt’ is like this. It seems that you need to put the MD5 hash value in the password. It is also one way to put the MD5 hash value, but this time I wrote it in the URL as follows and executed the query with the password part commented out. [code]?id=admin'%23[/code] Cleared safely. Although ‘gremlin’ and ‘cobolt’ were SQL injection types that execute invalid queries, there are also types of enemies that parse correct passwords using blind SQL injection. There are a total of 49 problems of Lord of SQL Injection including ‘All Clear’. Even if you don't understand the problem, you can find many Korean explanations online.news, blog, internet, IT, software, hardware, web service, food, mobile, game, anime, note, GIGAZINE
- Table of Contents:

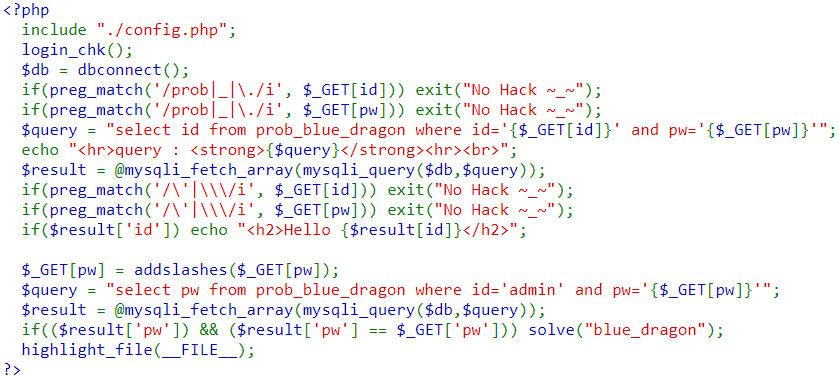
Solution: Lord of SQL Injection blue_dragon – niek
- Article author: niekdang.wordpress.com
- Reviews from users: 49009
Ratings
- Top rated: 3.0
- Lowest rated: 1
- Summary of article content: Articles about Solution: Lord of SQL Injection blue_dragon – niek Solution: Lord of SQL Injection blue_dragon. In this lab, we are not allowed to use quotes and backslash ( \ ). However, the query is executed before … …
- Most searched keywords: Whether you are looking for Solution: Lord of SQL Injection blue_dragon – niek Solution: Lord of SQL Injection blue_dragon. In this lab, we are not allowed to use quotes and backslash ( \ ). However, the query is executed before … In this lab, we are not allowed to use quotes and backslash (\). However, the query is executed before checking for these characters. We will use Time-based SQli with sleep() command to check if a condition is true or false. We use the payload ?id=admin’+and+if(length(pw)=1,sleep(1),0)# ?id=admin’+and+if(length(pw)=2,sleep(1),0)# ?id=admin’+and+if(length(pw)=3,sleep(1),0)# … to find the length of the password. Then, we…
- Table of Contents:
Leave a Reply Cancel reply
Post navigation
Categories
Lord of SQL Injection – Hell fire
- Article author: pywc.dev
- Reviews from users: 40187
Ratings
- Top rated: 4.8
- Lowest rated: 1
- Summary of article content: Articles about Lord of SQL Injection – Hell fire Lord of SQL Injection – Hell fire. by Paul Chung a year ago 3 min read. So… It seems that we’ve gotta find the email address for admin and the parameters … …
- Most searched keywords: Whether you are looking for Lord of SQL Injection – Hell fire Lord of SQL Injection – Hell fire. by Paul Chung a year ago 3 min read. So… It seems that we’ve gotta find the email address for admin and the parameters …
- Table of Contents:

See more articles in the same category here: Chewathai27.com/to/blog.
Lord of SQLInjection
! this site does not support IE _______________________ _______________________——————- `\ /:–__ | ||< > | ___________________________/ | \__/_________________——————- | | | | The Lord of the SQLI : The Fellowship of the SQLI, 2021 | | | | | | [enter to the dungeon] | | | | | | [RULE] | | – do not attack other database | | – do not exploit server | | – do not dos server [rubiya] | | ____________________|_ | ___________________————————- `\ |/`–_ | ||[ ]|| ___________________/ \===/___________________————————–
id :
pw :
Lord of SQL injections
Wolfman challenge:
As white spaces should not be used I used () for bypassing the spaces
To clear the level id should be admin
So injection is :
‘or(id=’admin’)or’
Results in clearing the level
Coming to DARKELF
The challenge is simple we should not use or (or) and so we can use ||
And the id should be admin
Injection:
‘ || (id=’admin’) — –
ORGE:
In this challenge usage of or ,and if forbidden and we have to crack the password when ever the injection is right it pops up displaying Hello guest so it’s a boolean based
We have to brute force the password
I did the brute forcing with Burpsuite
I used Burp suite to do the bruteforce no script can do it by script but used burp so as could do it faster.
when ever there is a change in the response it indicates that the injection worked and the page popped out Hello Guest
After the bruteforcing the Pw=6c864dec
Job done!
Coming to TROLL and Vampire :
It’s simple it matches the regular expression admin,
If we give id=AdMiN We can bypass the filter
SKELETON:
The query ends with 1 and 0 which returns false so we have to comment out those,next step is to give id as admin
Injection:
pw=’ or (id=’admin’) — – Does the job
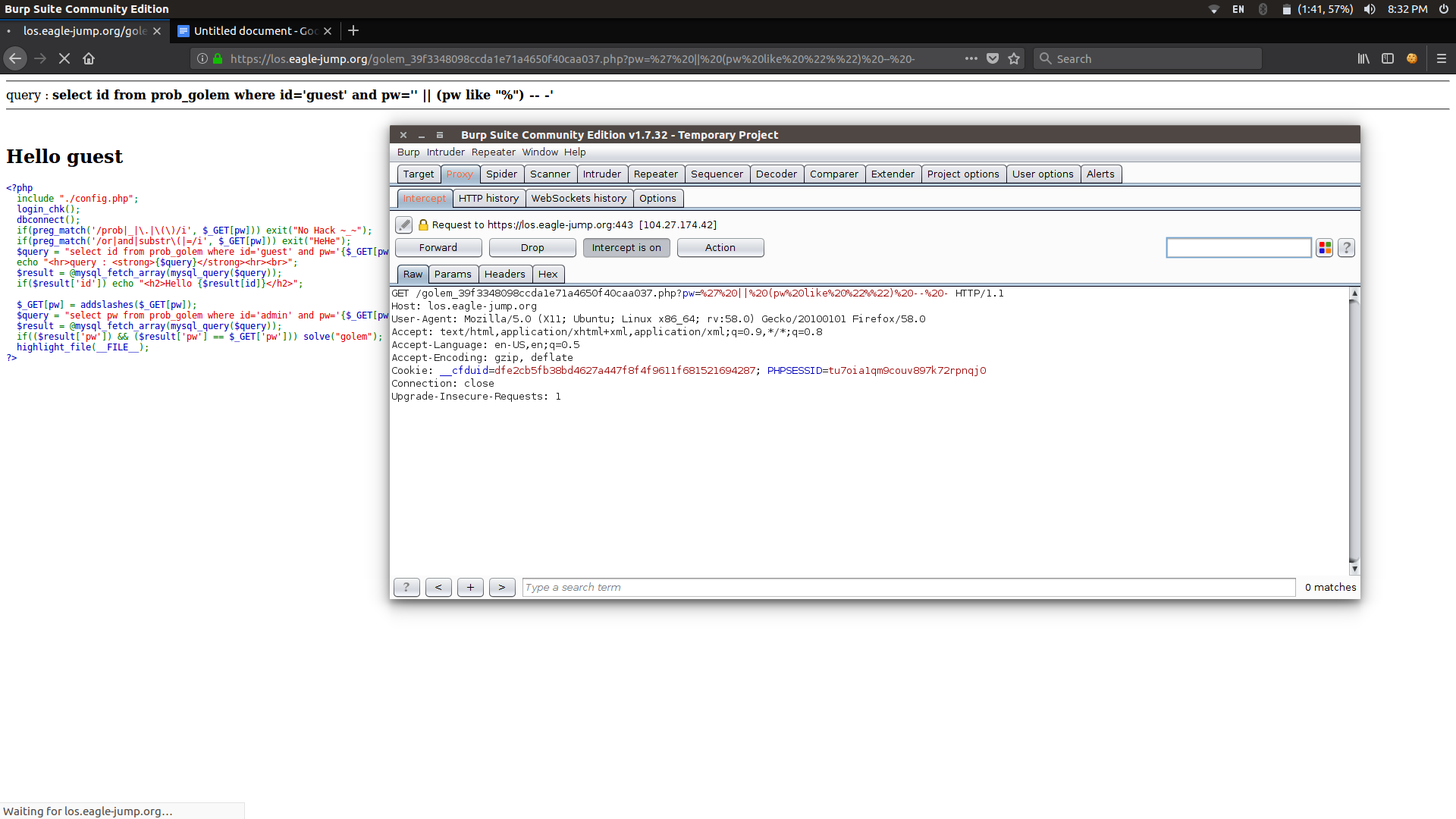
GOLEM:
In this problem we can’t use and,or,substr first we come out of pw giving a single quote
And inject our parameters there
So pw=’ || 1 — – breaks the query
At the place of 1 we give our query as (pw like “%”) — –
We have to brute force at the place before %
If the pw is abc , a% returns a True value
So I used burp to brute force:
After bruteforcing pw=88e3137f
Darkknight:
Here we have to give two parameters pw and no
Leaving pw empty and giving no=1 or 1 Breaks the query
Hence A boolean based injection and we have to find the password again
By bruteforcing: pw=1c62ba6f
‘Lord of SQL Injection’, a site where you can learn about SQL injection vulnerabilities while capturing dungeons
Aug 23, 2020 23:00:00
‘Lord of SQL Injection’, a site where you can learn about SQL injection vulnerabilities while capturing dungeons
An attack that manipulates the database illegally by executing a character string that the application does not expect is called
SQL injection, and there areimportant personal information such as credit card information and address was leaked by the attack. ” is a website that captures dungeons by making full use of such SQL injection.First, access Lord of SQL Injection and click ‘[enter to the dungeon]’.
It’s my first time to use Lord of SQL Injection, so click ‘Join’.
Enter the ID, email address, and password used in Lord of SQL Injection and click ‘Join’.
Enter the ID and password you registered earlier and click ‘Login’.
The screen to select the enemy is displayed. Click on the first enemy ‘gremlin’.
The SQL query executed on the website and the PHP code are displayed. While referring to the PHP code, you can defeat the enemy if you can execute invalid SQL queries.
In this problem, you can execute a query that returns some value, so add ‘?id=admin&pw=’ or ‘1’ = ‘1’ to the URL and execute.
‘GREMLIN Clear!’ is displayed and I was able to defeat the enemy safely.
If you solve the problem and defeat the enemy, you will proceed to a new enemy.
The problem of ‘cobolt’ is like this. It seems that you need to put the
MD5 hash value in the password.
It is also one way to put the MD5 hash value, but this time I wrote it in the URL as follows and executed the query with the password part commented out.
[code]?id=admin’%23[/code]Cleared safely.
Although ‘gremlin’ and ‘cobolt’ were SQL injection types that execute invalid queries, there are also types of enemies that parse correct passwords using blind SQL injection.
There are a total of 49 problems of Lord of SQL Injection including ‘All Clear’. Even if you don’t understand the problem, you can find many Korean explanations online.
So you have finished reading the lord of sql injection topic article, if you find this article useful, please share it. Thank you very much. See more: SQL injection cheat sheet, Lord of SQLI, SQL injection order by, SQL injection payload, SQL injection bypass filter, Lord of SQLInjection, SQL injection string, SQL injection – Filter bypass (Root me)

